Tags: swampctf2019
Rating: 5.0
### Problem Description
[Meanwhile at the NSA on a Friday afternoon]
Manager: Hey, we're going to be releasing our internal video training for Ghidra and we need you to watch it all to flag any content that needs to be redacted before release.
Manager: The release is next Monday. Hope you didn't have any weekend plans!
You: Uhhh, sure bu-
Manager: Great! Thanks. Make sure nothing gets out.
You: ... [looks at clock. It reads 3:45PM]
You: [Mutters to self] No way am I watching all of this: https://static.swampctf.com/ghidra_nsa_training.mp4
-= Created by DigitalCold =-
- - - -
### Solution
I downloaded the video from the provided [link](https://static.swampctf.com/ghidra_nsa_training.mp4).
After having it downloaded, I extracted 1 frame for each second of video using the [ffmpeg](https://ffmpeg.org/ffmpeg.html) tool.
```
$ ffmpeg -i ghidra_nsa_training.mp4 -vf "fps=1" out%0d.png
```
Once having all the frames extracted, I used [tesseract](https://es.wikipedia.org/wiki/Tesseract_OCR), an OCR engine to extract text from images to analyze all the frames previously extracted. The simple bash script I prepare for that:
```
for file in $(ls . | grep png); do
echo "image:${file}";
tesseract $file - | grep -i flag
done
```
I obtained the first part of the flag in the image out12175.png, as shown in the following image:
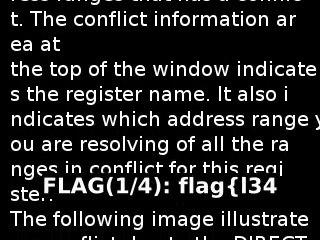
The next part of the flag was obtained in the image out26715.png:

All the parts of the flag were:
* FLAG(1/4): flag{l34
* FLAG(2/4): kfr33_n4
* FLAG(3/4): tion4l_s
* FLAG(4/4): 3cur1ty}
Flag: **flag{l34kfr33_n4tion4l_s3cur1ty}**
This is neat, well done, but kinda slow unless you have a high speed computer.