Tags: swampctf2019
Rating:
### Problem Description
The network investigative technique had just triggered and we were starting receive telemetry when, suddenly, a pop-up asked him for administrative access. He freaked out and yanked his cable leaving us with a copious amount of line noise. We've been tracking this guy for a while and really need a win here.
See if you can get anything out of this mess:
A7]^gF*(u(BkVO)1MV#U/oPWADf.4LBQ&)IE+j2TD.GLe2e4XS@q%-(3+b!&3+=g#AMcDXAMuMZ@:V/M2e4jY
-= Created by v0ldemort =-
- - - -
### Solution
We received a ciphered/encoded string, "A7]^gF*(u(BkVO)1MV#U/oPWADf.4LBQ&)IE+j2TD.GLe2e4XS@q%-(3+b!&3+=g#AMcDXAMuMZ@:V/M2e4jY". After trying to decipher it using many Cipher algorithms, I found the solution. It was encoded using [Base85](https://en.wikipedia.org/wiki/Ascii85):
I used [CyberChef](https://gchq.github.io/CyberChef) to decode the string obtaining an onion link _depastedihrn3jtw.onion/show.php?md5=7d1ecb0f8f428b70e49de68ead337d7e_:
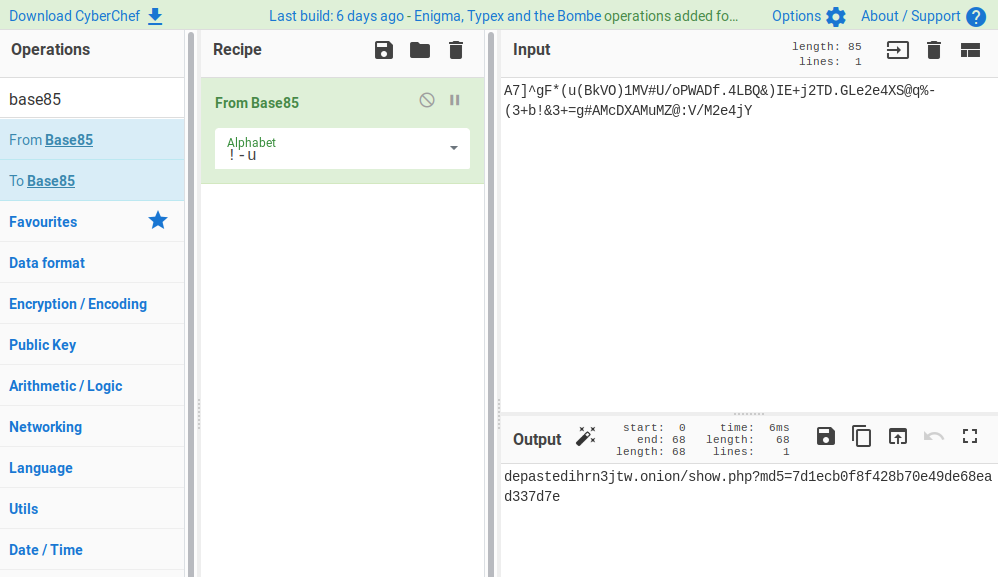
This link shows the following information in the comments:
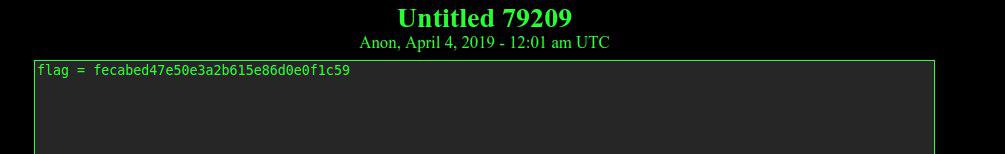
The comment with "flag = fecabed47e50e3a2b615e86d0e0f1c59" suggested me to visit the following onion link _depastedihrn3jtw.onion/show.php?md5=fecabed47e50e3a2b615e86d0e0f1c59_, which finally shows the flag:
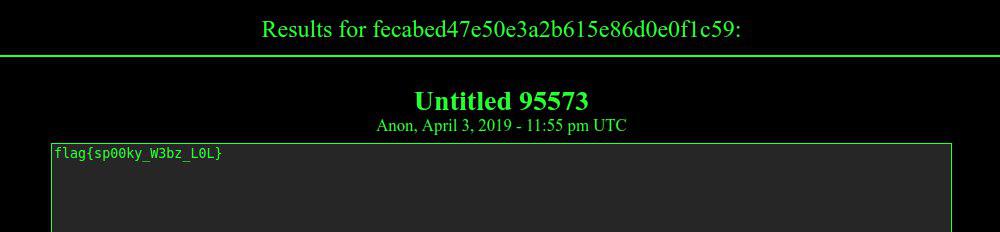
Flag: **flag{sp00ky_W3bz_L0L}**