Tags: infiltration forensics
Rating:
# Eternally Pwned: Infiltration
> Author: dree_
> Description: I recently had my passwords and other sensitive data leaked, but I have no idea how. Can you figure out how the attacker got in to my PC?
[network-capture.pcap](https://github.com/nopedawn/CTF/blob/main/WolvCTF24/Infiltration/network-capture.pcap)
Given the forensics challenge, we need to investigate data for evidence of network packet capture `network-capture.png`
We can investigate with Wireshark and analyze the every packet bytes, if we filter the most interraction is on `tcp` protocol & `smb` protocol. Both we're gonna focusing on (`tcp` / `smb`) packet interraction.
If we filter the packet in number `446` & `550`
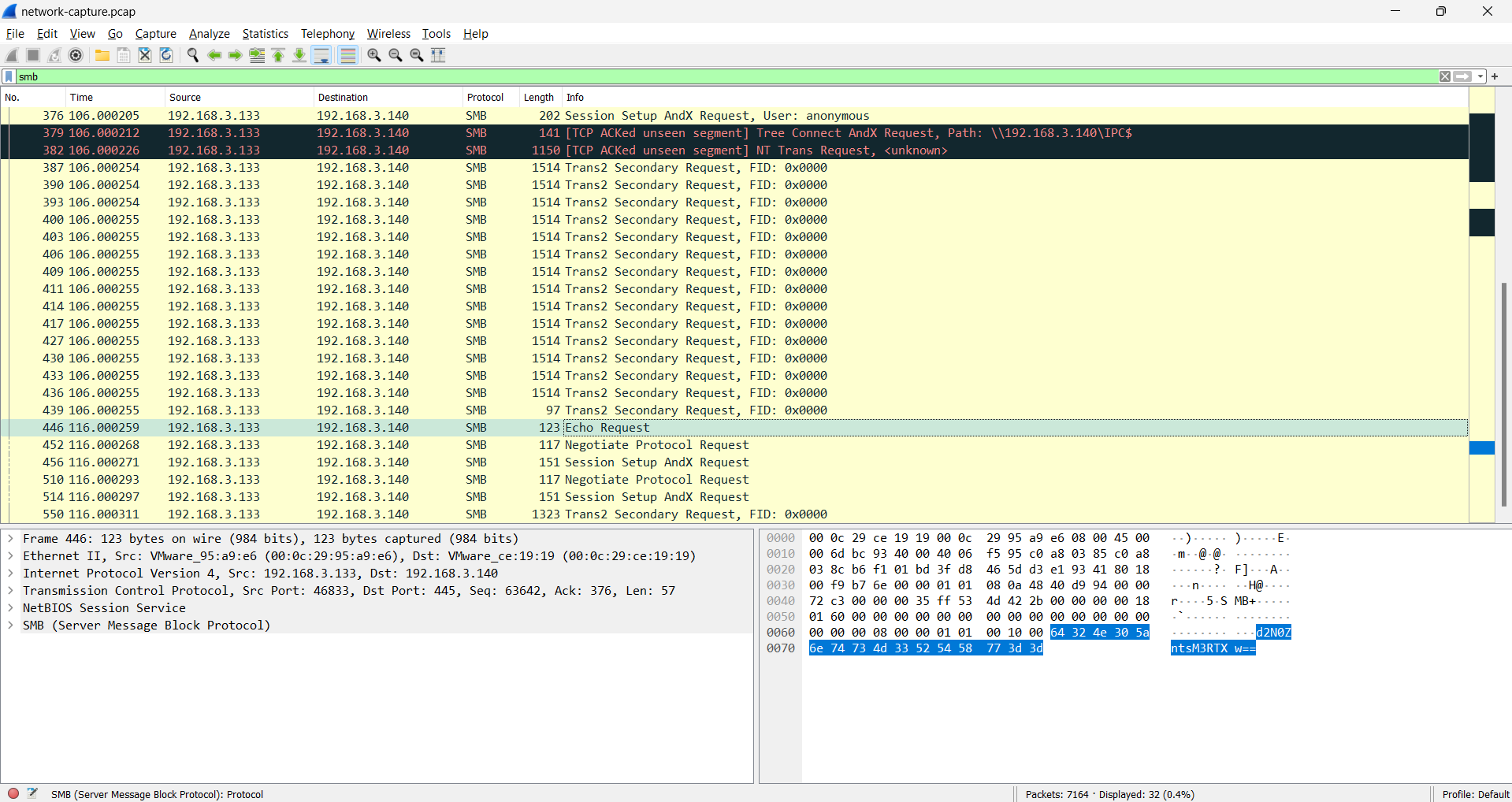
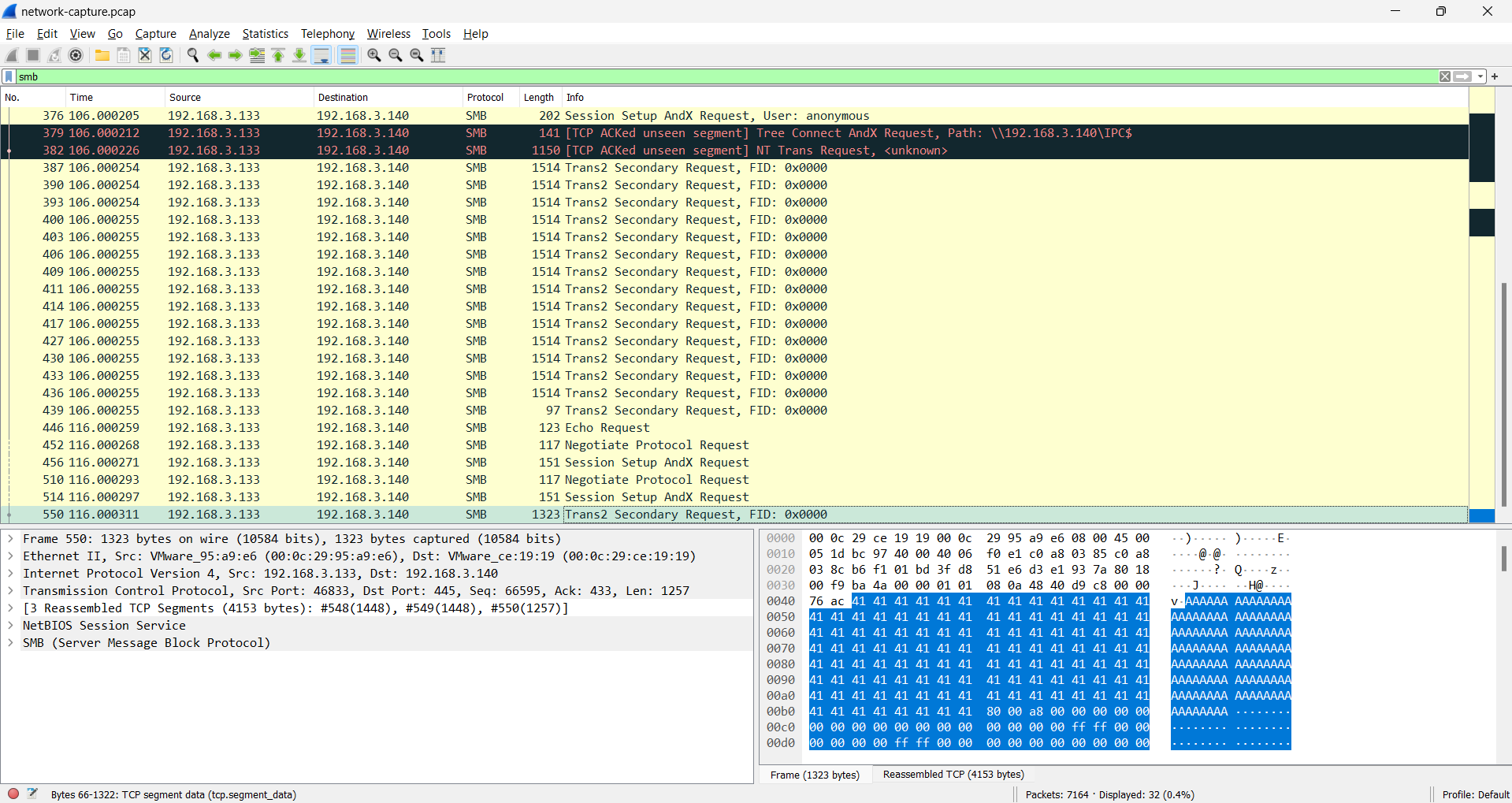
or filter `tcp.stream eq 4` (both are same filtering)
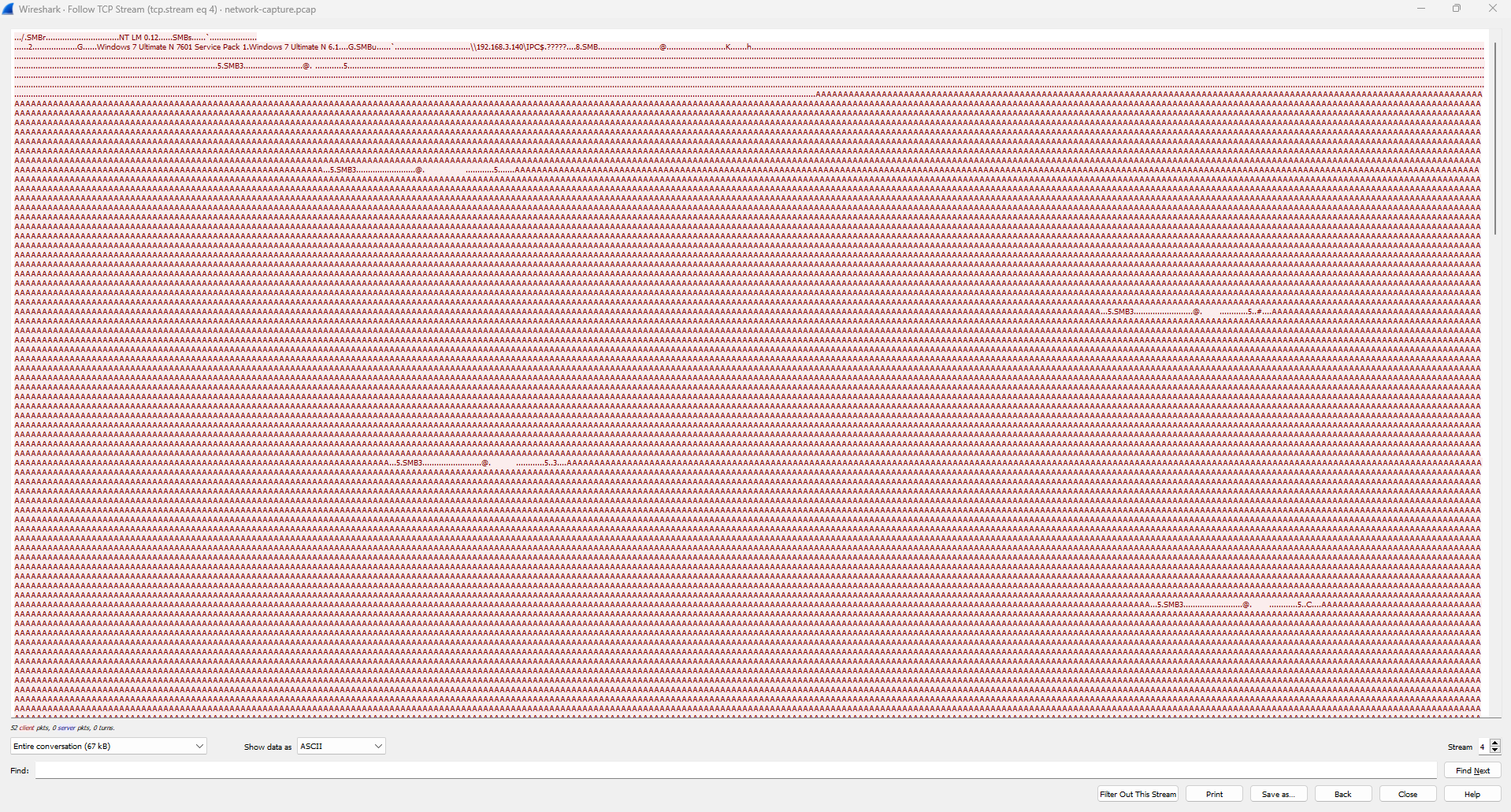
We can see the bunch of "A" characters, and if wee look closely there's look like a base64 string between the "A" characters
Note that we have found these, next we can grep the base64 string or using tshark
```bash
$ tshark -r network-capture.pcap -Y "frame.number == 446" -x
0000 00 0c 29 ce 19 19 00 0c 29 95 a9 e6 08 00 45 00 ..).....).....E.
0010 00 6d bc 93 40 00 40 06 f5 95 c0 a8 03 85 c0 a8 .m..@.@.........
0020 03 8c b6 f1 01 bd 3f d8 46 5d d3 e1 93 41 80 18 ......?.F]...A..
0030 00 f9 b7 6e 00 00 01 01 08 0a 48 40 d9 94 00 00 ...n......H@....
0040 72 c3 00 00 00 35 ff 53 4d 42 2b 00 00 00 00 18 r....5.SMB+.....
0050 01 60 00 00 00 00 00 00 00 00 00 00 00 00 00 00 .`..............
0060 00 00 00 08 00 00 01 01 00 10 00 64 32 4e 30 5a ...........d2N0Z
0070 6e 74 73 4d 33 52 54 58 77 3d 3d ntsM3RTXw==
$ echo "d2N0ZntsM3RTXw==" | base64 -d
wctf{l3tS_
```
We've got the first part `wctf{l3tS_`
```bash
$ tshark -r network-capture.pcap -Y "frame.number == 550" -x
0d20 41 41 41 41 4d 33 52 6c 55 6d 34 30 62 45 78 35 AAAAM3RlUm40bEx5
0d30 58 32 63 77 58 77 3d 3d 41 41 41 41 41 41 41 41 X2cwXw==AAAAAAAA
0f20 41 41 41 41 41 41 41 41 41 41 41 41 59 6b 78 56 AAAAAAAAAAAAYkxV
0f30 4d 31 38 33 62 6a 6c 33 62 54 52 70 56 32 35 4d M183bjl3bTRpV25M
0f40 66 51 3d 3d 41 41 41 41 41 41 41 41 41 41 41 41 fQ==AAAAAAAAAAAA
$ echo "M3RlUm40bEx5X2cwXw==" | base64 -d
3teRn4lLy_g0_
$ echo "YkxVM183bjl3bTRpV25MfQ==" | base64 -d
bLU3_7n9wm4iWnL}
```
then the two last part `3teRn4lLy_g0_` & `bLU3_7n9wm4iWnL}`
> Flag: `wctf{l3tS_3teRn4lLy_g0_bLU3_7n9wm4iWnL}`