Rating:
This is the last challenge of DFIR, which asked you to find another TCP connection that gain access to MogamBro machine. Remember that we have trace.pcap and it’s not be analyzed:
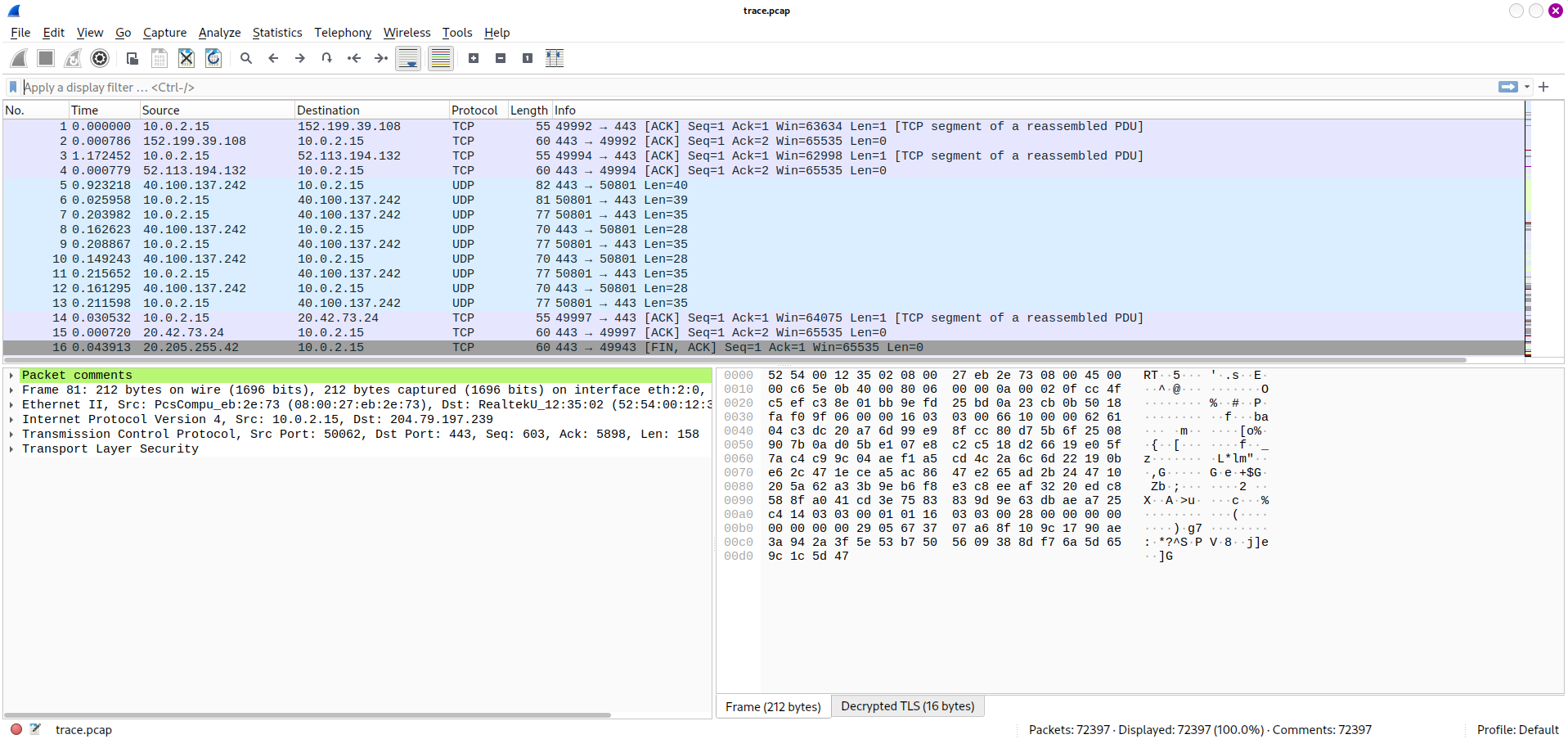
First, to know what’s another TCP connection, I need to know how many connections are there, so I checked in memory file by **windows.netscan plugins**:

After that, you will check each connections, but these addresses are HTTP2, so their requests and responses are encrypted. To decrypt it we need key, and fortunately I found it in Desktop which is same directory with **keylog.pcapng**:
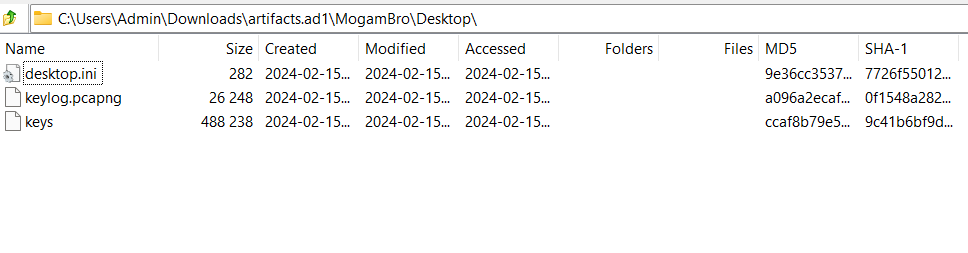
Now go to **Edit -> Preferences… -> Protocols -> Find TLS -> Import key -> Reload pcapng/pcap file**. And now we can read HTTP2/TLS packets, return to our mission, we need to read each connections to see if connections is suspicious and not in result of netscan. It took me a lot of time, and I found a connection which is not in netscan and it contains many pastebin links, also the flag ?:
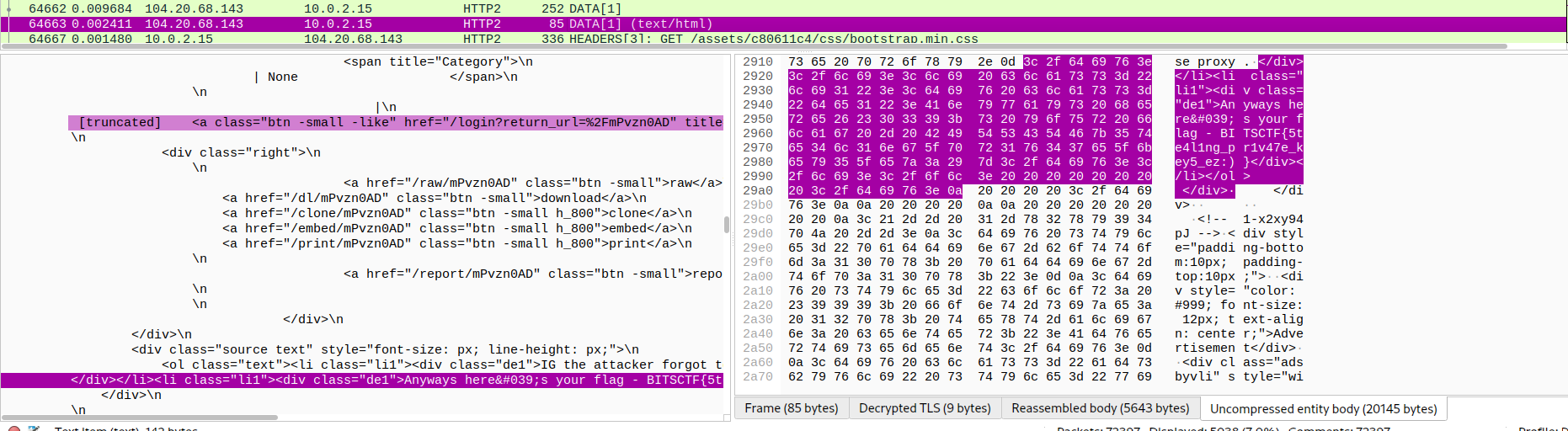
**FLAG: BITSCTF{5te4l1ng_pr1v47e_key5_ez:) }**