Rating:
Challenge: **Image Extraction**
Category: **Forensics**
Points: **150**
Description: **Uncover a jpg file from the given file. The flag is in that image.**
Solution: **analyzing the hex of the file, I used [Hexed](https://hexed.it/) , we could guess that the magic bytes had been changed, in reality it was not a pdf but a zip**
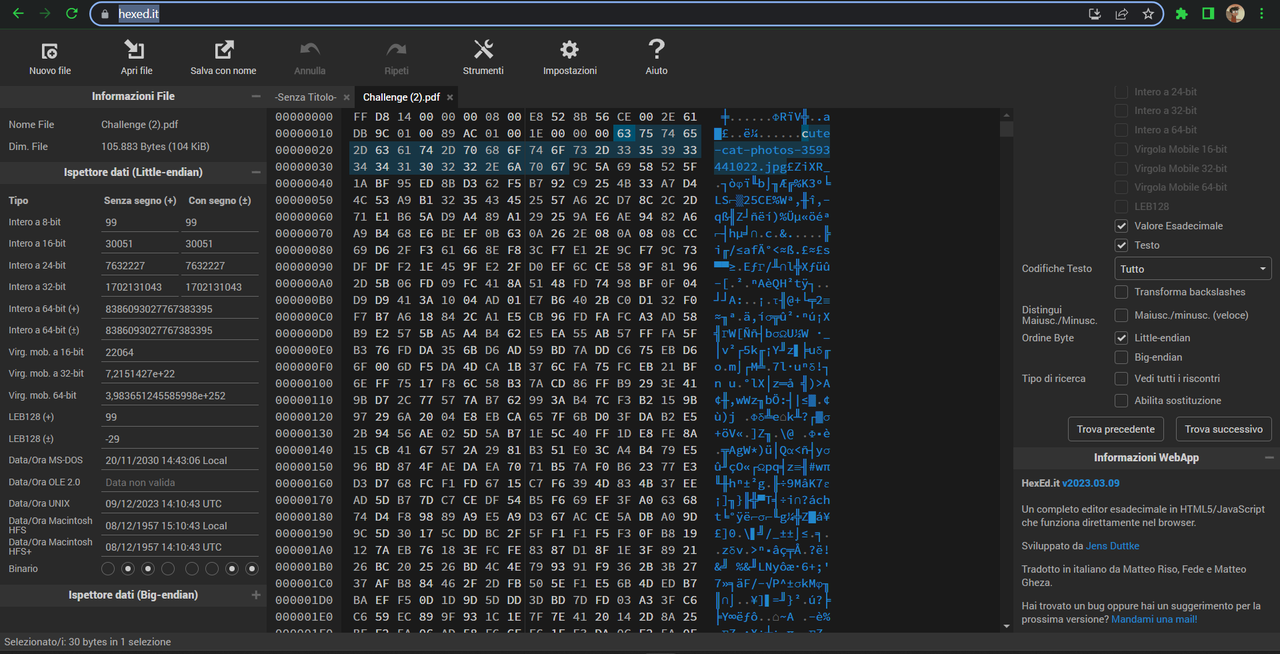
**changing the magic bytes to those of a zip archive, we could export it, extract it and we had the image with numbers: 74 65 78 73 61 77 7B 6F 4E 65 5F 43 75 54 65 5F 43 61 54 21 7D (they are the flag in hex)**

**at this point it was enough to convert from hex to text, I used [CyberChef](https://gchq.github.io/CyberChef/#recipe=From_Hex('Space')&input=NzQgNjUgNzggNzMgNjEgNzcgN0IgNkYgNEUgNjUgNUYgNDMgNzUgNTQgNjUgNUYgNDMgNjEgNTQgMjEgN0Q)**
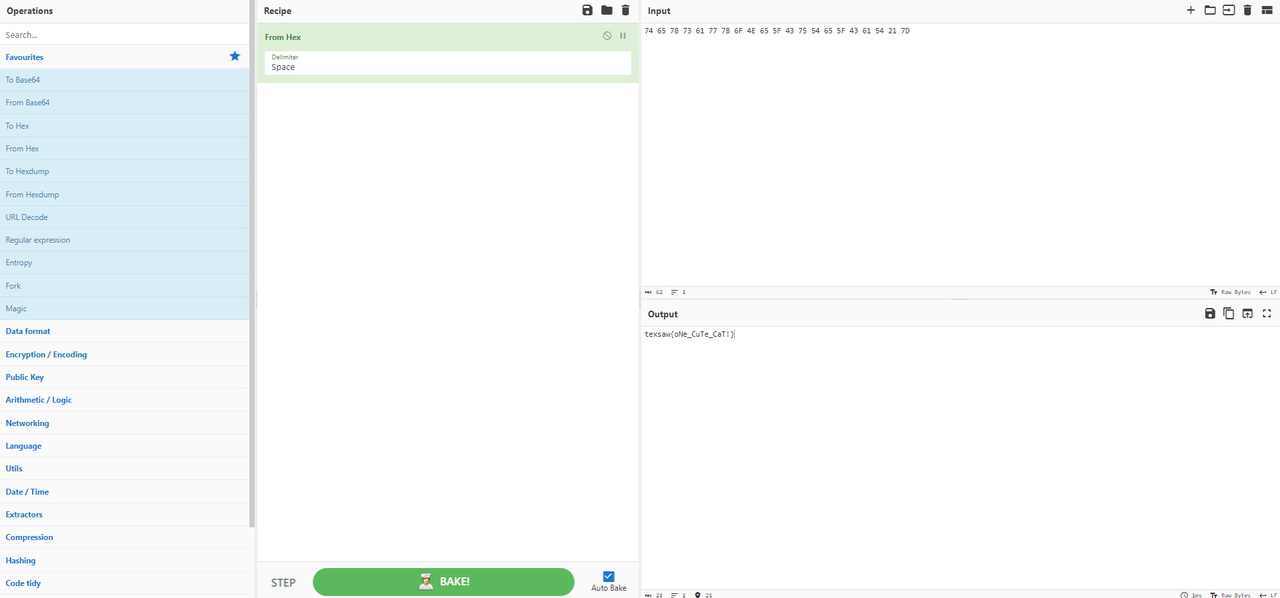
flag: **texsaw{oNe_CuTe_CaT!}**