Tags: wireshark
Rating: 5.0
This was a fairly simple wireshark packet analysis challenge. For this challenge, we were given the following description:
We were given a link to download a PCAPNG file. This is the file that we will need to examine in order to retrieve our flag.
## Open the file with wireshark-->
Since this is a packet capture file, we will go ahead and open it up with wireshark. In the packet list pane, we have a lot of packets displayed.
We aren't going to need all of these as we already have a hint as to what we are looking for. We can go ahead and narrow our search down to only TCP protocol using the filter toolbar...
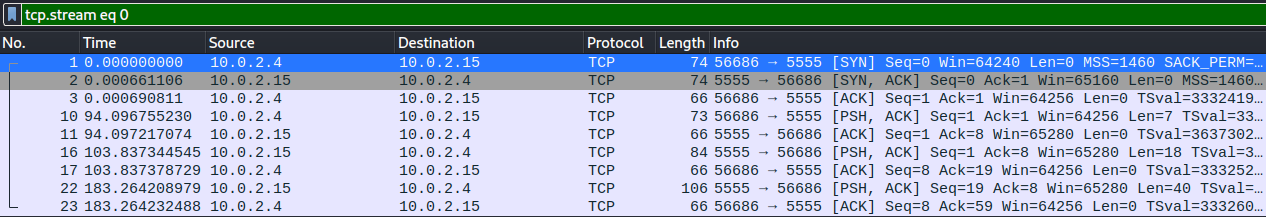
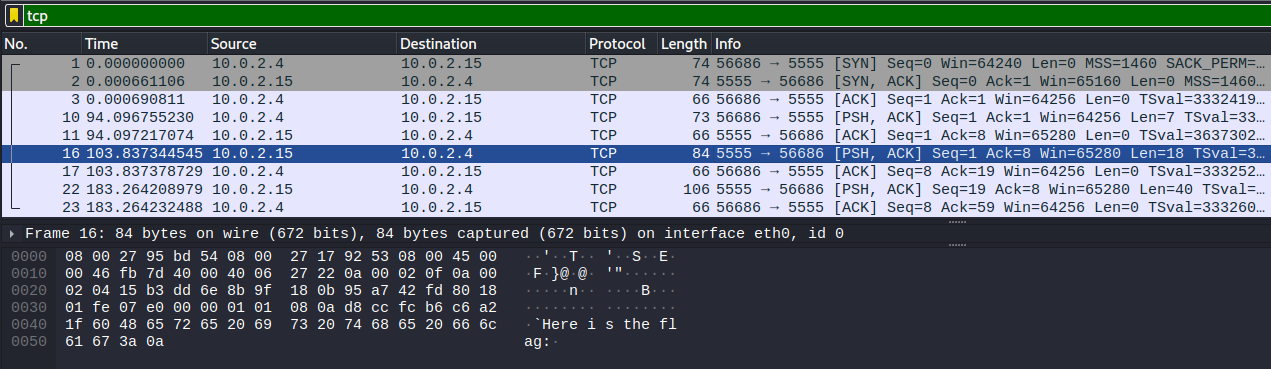
Now that we have our results filtered, let's scroll through a few of the packets in the list and pay attention to packet bytes pane for anything that may give us some more information about what is being passed in these packets.
As we scroll through, we land on one that gives us some plaintext regarding the flag.
## Follow the stream-->
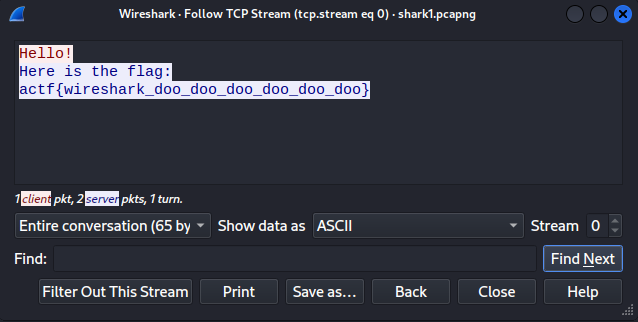
Since we know the packets contain plaintext, we can just right click on the packet and select follow stream and it will give it all to us in a readable format.
And there is our flag...