Tags: web npm nodejs
Rating:
## SpiralCI (496 pts - 23 solves) write up
This was a good challenge, it uses a new attack technique called Dependency Confusing Attack.
Web interfaces:
I looked at the cookie and got a jwt:
```
spiralCI=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyaWQiOi0xfQ.pCIT8y2m4E3nC-rpos3BvorxYZqIDpNNdZroYvpzMYI
```
After fuzzing and finding other interfaces to attack, i found nothing so i decided to attack on JWT.
Using jwt.io:
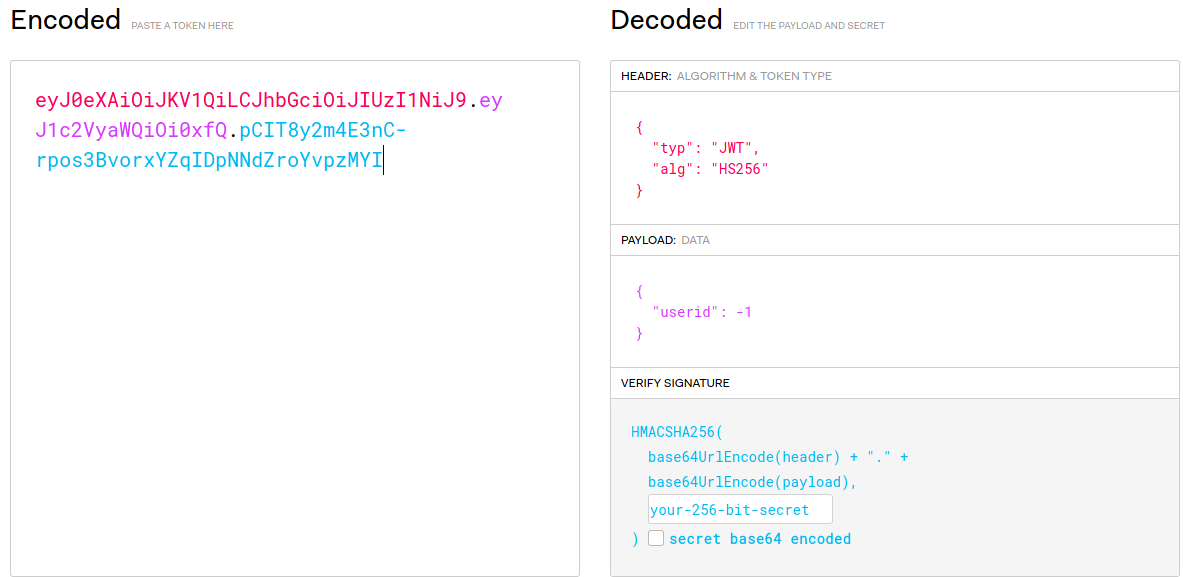
So i tried modify jwt's algorithm to none and userid to 1.
Then i got this:

Seems like it's an admin account and it's disabled, so i changed userid to 2
```
spiralCI=eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0.eyJ1c2VyaWQiOjJ9.
```
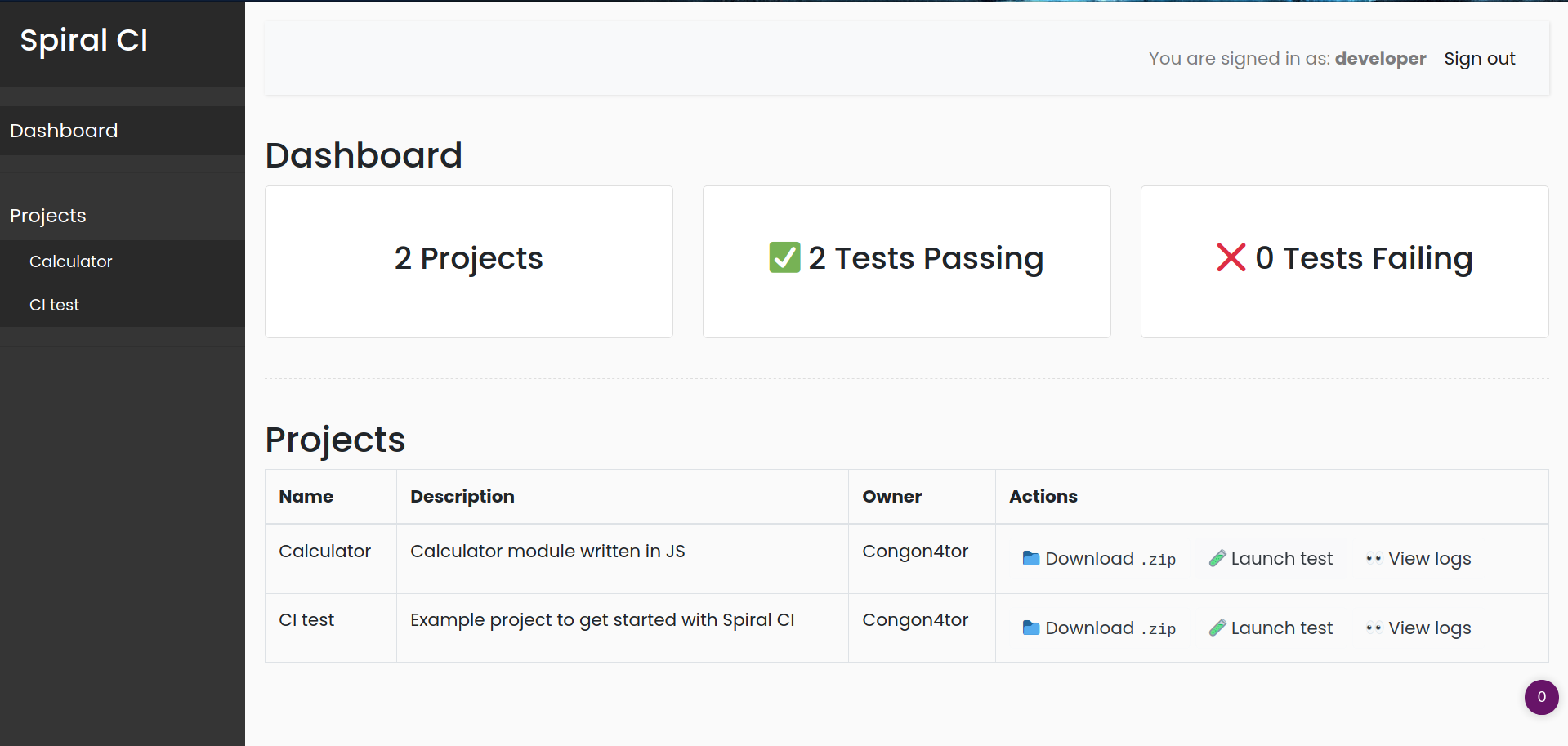
So it worked, so basically there are two Nodejs packages, and the chall let me run the CI test and view their logs. So i downloaded the zip files.
They are basically two simple Nodejs projects, and there are an important file package.json in 'calculator' package
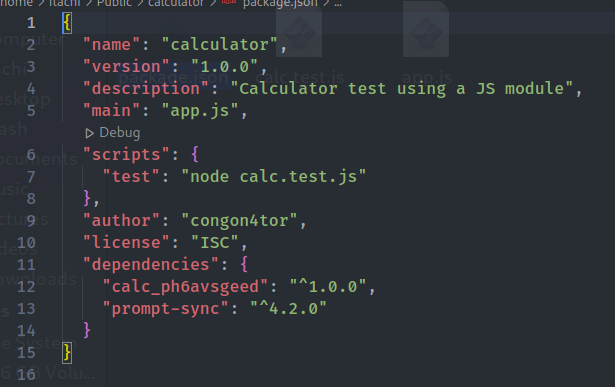
Then i tried running the 'calculator' project and view it's log.
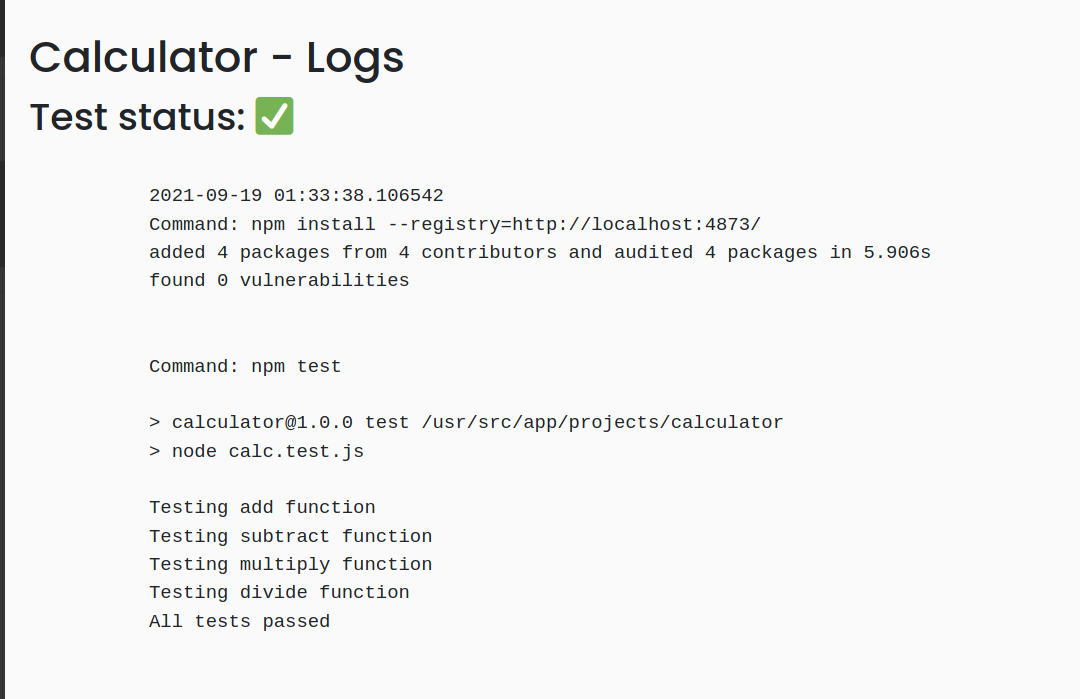
First idea of mine was to overwrite the script in package.json to read the flag. But after finding for a while, i found nothing, i can't modify the project because they are admin's projects.
Admin account was disabled so i can't log in as admin either.
Then i decided to look at other chall and comeback with it later
After starting do this chall again, i found out that the package "calc_ph6avsgeed" (in this write up i will use the same package tho) was used in the last time now has a different name. So i think this package maybe my entry to find the flag.
The logs show that the project used private registry, so i was thinking of a way to takeover the package with npm public module.
And then i found this article: https://digital.nhs.uk/cyber-alerts/2021/cc-3751
And this about how to publish a npm module: https://zellwk.com/blog/publish-to-npm/
So i created a npm package with the name "calc_ph6avsgeed" and version: 1.0.1 and the "preinstall" script to list the file in current folder.
Then publishing it to npm public registry.
I got the following result:
So we got RCE on server
Looks at the path to pwd, after listing for a while, i found the flag is located at /usr/src/app/flag.txt
And launch the test, then view the log:
P/s: Dont't forget to give me a star if you find it's useful xD