Tags: reversing
Rating:
## UTCTF_Crackme
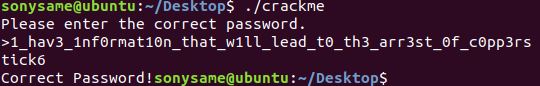
We need to know the correct password!
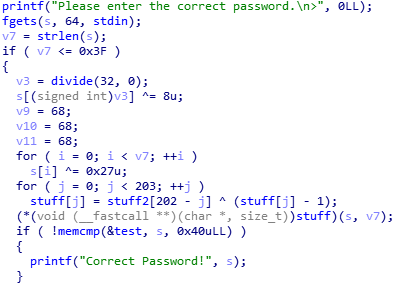
We already know *stuff*, *stuff2*, and *test*.
*stuff* is used as a function. So we need to change the binary(*stuff*) into assembly code.
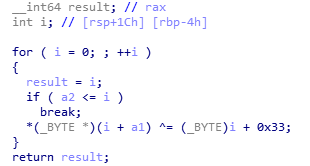
This is the binary of *stuff* ,assembly code, and c-pseudo code.
**Array Literal:**
{ 0x55, 0x48, 0x89, 0xE5, 0x48, 0x89, 0x7D, 0xE8, 0x48, 0x89, 0x75, 0xE0, 0xC7, 0x45, 0xFC, 0x00, 0x00, 0x00, 0x00, 0xE9, 0xA1, 0x00, 0x00, 0x00, 0x8B, 0x45, 0xFC, 0x83, 0xC0, 0x41, 0x89, 0x45, 0xF0, 0xC7, 0x45, 0xF4, 0x20, 0x00, 0x00, 0x00, 0xC7, 0x45, 0xF8, 0x05, 0x00, 0x00, 0x00, 0x8B, 0x45, 0xF4, 0x89, 0xC2, 0xC1, 0xEA, 0x1F, 0x01, 0xD0, 0xD1, 0xF8, 0x89, 0xC2, 0x8B, 0x45, 0xF8, 0x8D, 0x0C, 0x02, 0xBA, 0x93, 0x24, 0x49, 0x92, 0x89, 0xC8, 0xF7, 0xEA, 0x8D, 0x04, 0x0A, 0xC1, 0xF8, 0x02, 0x89, 0xC2, 0x89, 0xC8, 0xC1, 0xF8, 0x1F, 0x29, 0xC2, 0x89, 0xD0, 0x89, 0xC2, 0xC1, 0xE2, 0x03, 0x29, 0xC2, 0x89, 0xC8, 0x29, 0xD0, 0x83, 0xF8, 0x02, 0x75, 0x0E, 0x8B, 0x45, 0xF0, 0x8B, 0x45, 0xF0, 0x83, 0xE8, 0x04, 0x89, 0x45, 0xF0, 0xEB, 0x12, 0x8B, 0x45, 0xF0, 0x83, 0xE8, 0x41, 0x89, 0x45, 0xF0, 0x8B, 0x45, 0xF0, 0x83, 0xC0, 0x33, 0x89, 0x45, 0xF0, 0x8B, 0x45, 0xF0, 0x8B, 0x55, 0xFC, 0x48, 0x63, 0xCA, 0x48, 0x8B, 0x55, 0xE8, 0x48, 0x01, 0xCA, 0x0F, 0xB6, 0x0A, 0x89, 0xC6, 0x8B, 0x45, 0xFC, 0x48, 0x63, 0xD0, 0x48, 0x8B, 0x45, 0xE8, 0x48, 0x01, 0xD0, 0x31, 0xF1, 0x89, 0xCA, 0x88, 0x10, 0x83, 0x45, 0xFC, 0x01, 0x8B, 0x45, 0xFC, 0x48, 0x98, 0x48, 0x39, 0x45, 0xE0, 0x0F, 0x87, 0x50, 0xFF, 0xFF, 0xFF, 0x90, 0x5D, 0xC3, 0x00, 0x00, 0x00, 0x00 }
**Disassembly:**
push rbp
mov rbp,rsp
mov QWORD PTR [rbp-0x18],rdi
mov QWORD PTR [rbp-0x20],rsi
mov DWORD PTR [rbp-0x4],0x0
jmp 0xb9
mov eax,DWORD PTR [rbp-0x4]
add eax,0x41
mov DWORD PTR [rbp-0x10],eax
mov DWORD PTR [rbp-0xc],0x20
mov DWORD PTR [rbp-0x8],0x5
mov eax,DWORD PTR [rbp-0xc]
mov edx,eax
shr edx,0x1f
add eax,edx
sar eax,1
mov edx,eax
mov eax,DWORD PTR [rbp-0x8]
lea ecx,[rdx+rax*1]
mov edx,0x92492493
mov eax,ecx
imul edx
lea eax,[rdx+rcx*1]
sar eax,0x2
mov edx,eax
mov eax,ecx
sar eax,0x1f
sub edx,eax
mov eax,edx
mov edx,eax
shl edx,0x3
sub edx,eax
mov eax,ecx
sub eax,edx
cmp eax,0x2
jne 0x7b
mov eax,DWORD PTR [rbp-0x10]
mov eax,DWORD PTR [rbp-0x10]
sub eax,0x4
mov DWORD PTR [rbp-0x10],eax
jmp 0x8d
mov eax,DWORD PTR [rbp-0x10]
sub eax,0x41
mov DWORD PTR [rbp-0x10],eax
mov eax,DWORD PTR [rbp-0x10]
add eax,0x33
mov DWORD PTR [rbp-0x10],eax
mov eax,DWORD PTR [rbp-0x10]
mov edx,DWORD PTR [rbp-0x4]
movsxd rcx,edx
mov rdx,QWORD PTR [rbp-0x18]
add rdx,rcx
movzx ecx,BYTE PTR [rdx]
mov esi,eax
mov eax,DWORD PTR [rbp-0x4]
movsxd rdx,eax
mov rax,QWORD PTR [rbp-0x18]
add rax,rdx
xor ecx,esi
mov edx,ecx
mov BYTE PTR [rax],dl
add DWORD PTR [rbp-0x4],0x1
mov eax,DWORD PTR [rbp-0x4]
cdqe
cmp QWORD PTR [rbp-0x20],rax
ja 0x18
nop
pop rbp

By calculating in reverse, we can get the string
**1_hav3_1nf0rmat10n_that_w1ll_lead_t0_th3_arr3st?0f_cspp3rstick6**
Something is strange!
divide(32,0) makes exception, but the ida doesn't show the try-catch clause.
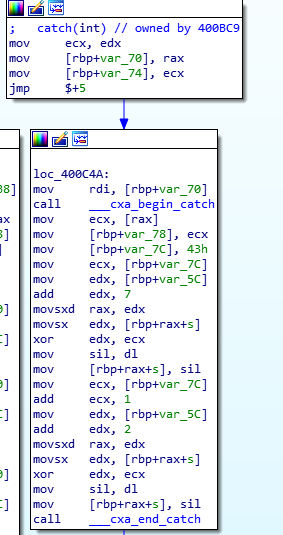
This means...
input[52]^=0x43
input[47]^=0x44
Finally, we can get the correct password