Tags: crypto aes
Rating: 5.0
**This is just an overview of the solution, for the full details of the solution look at the URL.**
## Solution Overview
Reading the code, it is easy to see that getting the flag requires as to do two things:
1. Send an ciphertext that decrypts to `gimme_flag` to get the encrypted flag
2. Decrypt the flag
Although _AES_ is set to _ECB_, a custom encryption mode is used, with padding. There is also a __decryption oracle__, since we can validate if `decrypt(cipher)==plaintext`. All these will be used to find craft the desired ciphertext and decrypt the flag.
We can analyze the `tsb_decrypt(msg)` function
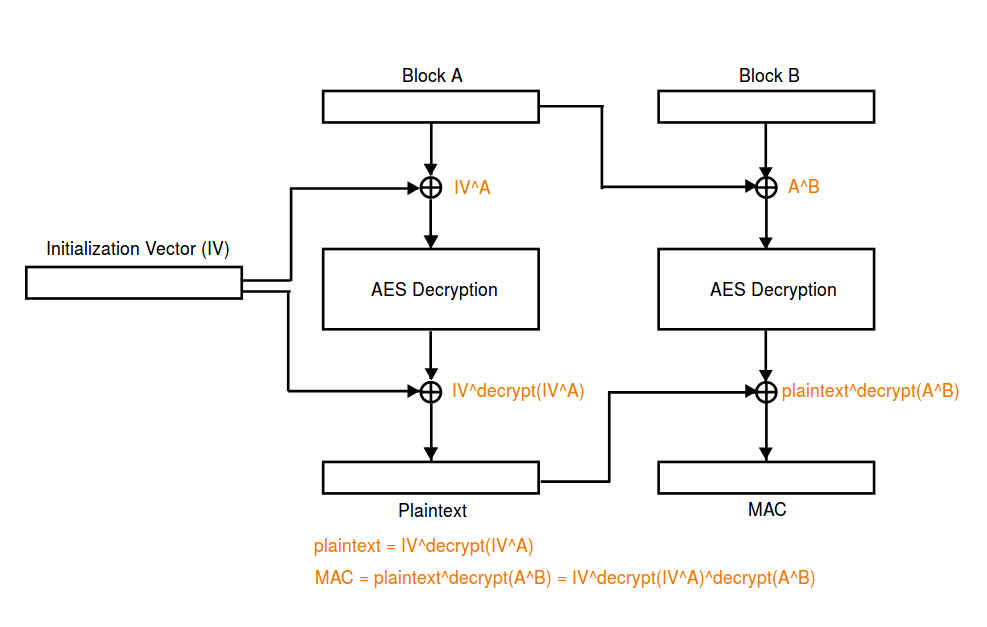
By constructing the ciphertext in the form `(IV, C^IV, IV)` then __the plaintext will always be `plaintext=IV^decrypt(C)` with a proper MAC__.
We modify the IV to manipulate the padding and this allows us to brute force the byte by byte. We craft a message with plaintext `gimme_flag` and decrypt the flag.